| Sooo are we headed for..... on 11:23 - May 5 by gordon |
Have they convincingly explained why they're using a centralised government held database?
Surely it will just mean that because of legitimate security concerns, not enough people will be convinced to download it - I can't imagine I'll want anything to do with it from what I've heard so far. |
They do list pros and cons in the article.
Simply put.
In the decentralised model, there is less information because it can't be processed in centrally. From a computing standpoint that does make sense. So whilst in the strictest sense of the word the application would work, the NHS would not be able to find out anything else more useful other than a person is ill and these people have been near them.
Now depending on your goals, this may well be enough.
In a centralised model, you sacrifice having the anonymised data in a central location. This would allow the entity collecting that data to do aggregations from it, and gleam more useful information that you could not do with only subsets of the data.
There is a picture that sort of illustrates this here:
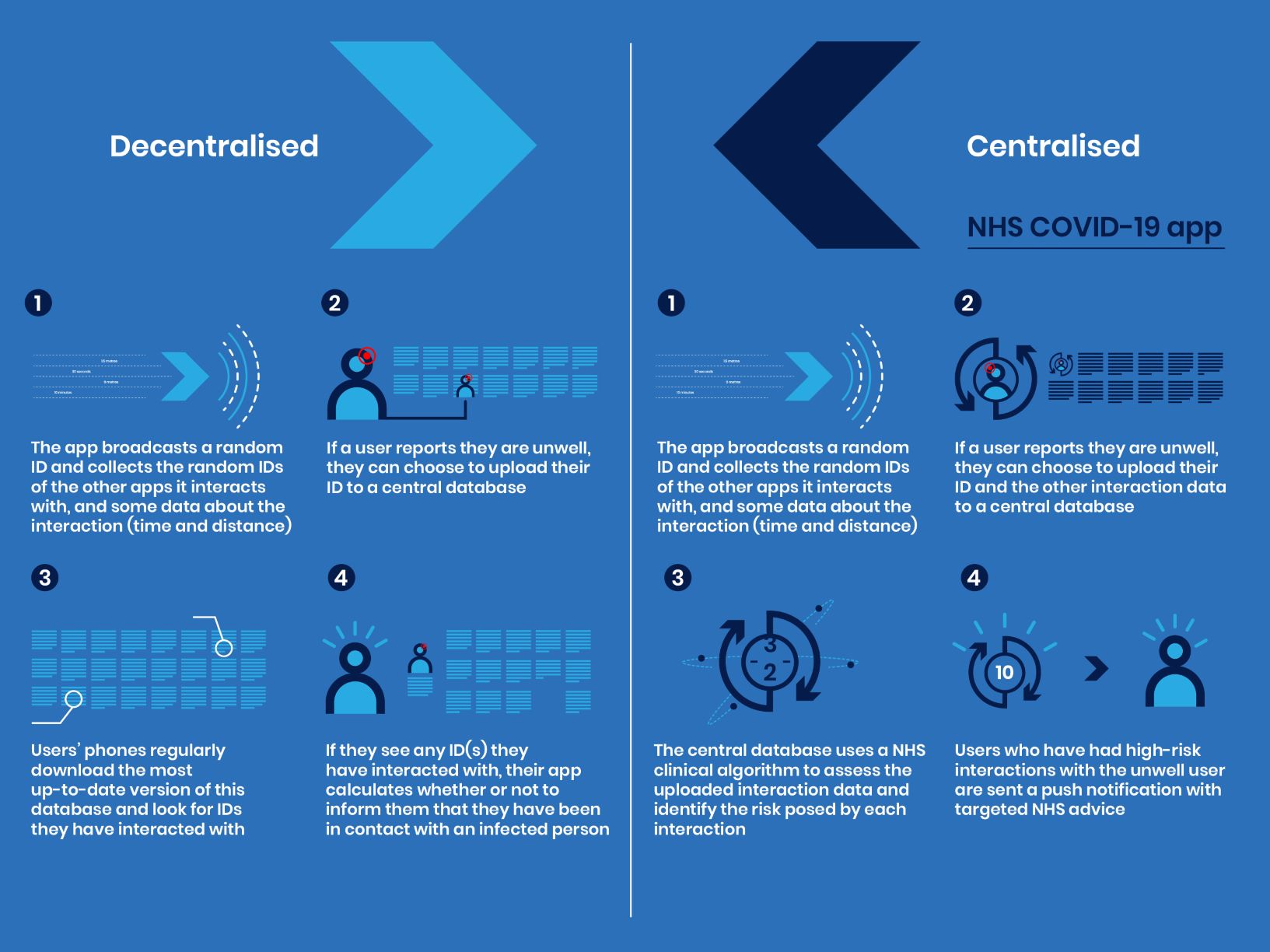
So now as far as security concerns, here is what I could gleam.
----
You start the app and get assigned what is called a GUID. Anyone who is familiar with software development will have come across these before and they look like this:
7bb0f988-6622-4e14-92a4-7c50dc3beb72.
Basically these are unique, "random" identifiers. The chances that two will be the same are absolutely tiny. That one I just created has probably never been seen before.
Anyway that is now you. They then record the first part of your post code and your phone model. At this point in the blog they say they've got nothing personal identifiable and take nothing more than that information. What I would say at this point is that I'd maybe slightly disagree, especially if you have a slightly rarer phone model and especially if they take any other operating system information that could potentially identify that as you.
Now you have that installed and the NHS has some data (ID, part of postcode, phone model / operating system), every day they encrypt your ID with some metadata they don't specify, with the key for this being held by the NHS I believe given how they've described it.
This is the information that is then shared between the phones, along with some other information that tries to work out how close you might have been. These are stored on the phones of the other person (still all encrypted). Assuming at this point nothing happens, after 28 days all the data is gone and nothing beyond the original information will have been sent to the NHS.
If you do catch something that is when you can choose to send that data to the NHS to be decrypted and used. If it finds any of the connections you made to other phones were at risk, they will be notified. At this point, without knowing what specifically is in those blobs, it's very hard to work out what information they have. I would say they should specify what it is they are recording but this will be decompiled I imagine within minutes of being on the app store(s) which should make it easy enough to see.
Their argument here is that now because they have all this information, they can create better risk models, which seems sensible.
So now the question becomes, how could you actually attack this? Well the first thing you theoretically need to be able to do is work out ID -> Person. You would need a copy of their ID or a whole subset of the NHS data which you would maybe be able to do something with but it's pretty tough and there's not a lot to go on, especially nothing that one would consider a huge issue. The NHS probably already have your name, phone number, address etc. Given the application apparently does not record any other biographical data, it would be quite hard to work out which ID is which person without being in close proximity.
Assuming the blog and accompanying paper are on the up and up and are not recording more than they say there are, there is not a lot to worry about here. You'd probably be able to gleam more off TWTD than this app could off you.
But until we can see the code in some form (which arguably should be open source), then people should exercise some caution. It will be established fairly quickly whether they were lying or not.
One other thing I do note is that in one of the select committees, they seemed fairly noncommittal on people being able to request their data is removed once this is over, and also that their data will not be sold at a later date which I don't think is right. There should be nothing that would stop people using this, trying to sell the data afterwards is ridiculous. I'd like to see what the ICO would do if the request was denied. |  |